In the evolving digital landscape, cybersecurity threats are becoming more sophisticated. Ethical hacking, also known as penetration testing, has emerged as a crucial method to safeguard systems and networks. Ethical hackers use a variety of tools to identify vulnerabilities, prevent potential breaches, and ensure data security. This article highlights 10 essential ethical hacking tools that professionals should master to stay ahead in the cybersecurity field.
Whether you’re an experienced ethical hacker or a beginner entering the cybersecurity domain, understanding these tools’ functionalities and applications is crucial. These tools not only enhance your skills but also provide robust solutions for testing and securing IT infrastructures. Below, we dive into the features, uses, and importance of each tool.
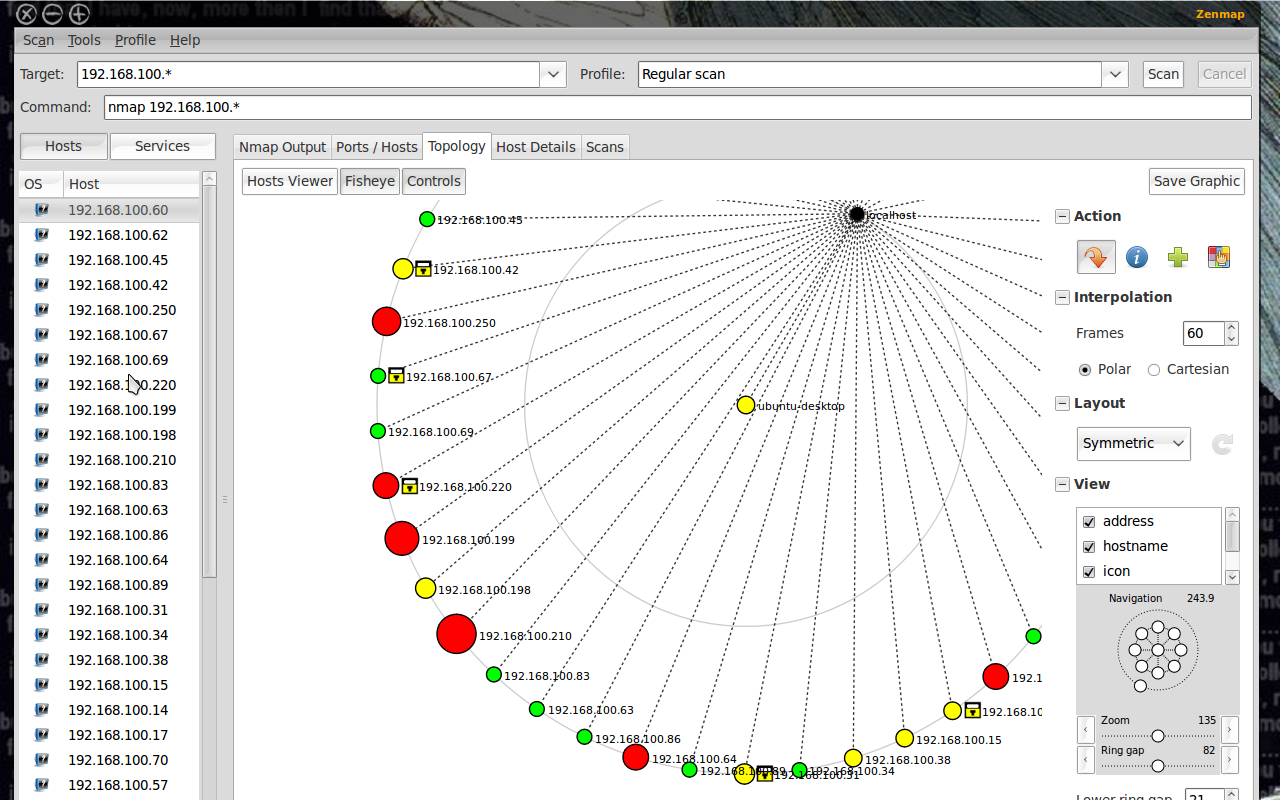
1. Nmap (Network Mapper)

Nmap, short for Network Mapper, is one of the most widely used tools in ethical hacking. This open-source utility is essential for network discovery and security auditing.
Key Features of Nmap
- Network Scanning: Nmap identifies active devices within a network and maps connections.
- Port Scanning: It detects open ports, revealing potential vulnerabilities.
- Flexibility: Supports a wide range of operating systems, including Windows, Linux, and macOS.
Why Ethical Hackers Use Nmap
Ethical hackers rely on Nmap to assess network configurations and identify weaknesses before attackers can exploit them. Its customizable scripts make it particularly effective in large-scale network analyses.
Example Use Case
Imagine an organization launching a new web server. An ethical hacker can use Nmap to ensure all unnecessary ports are closed, reducing the risk of unauthorized access.
2. Metasploit Framework
The Metasploit Framework is a powerful penetration testing tool that simplifies exploiting vulnerabilities in systems and applications.
Key Features of Metasploit
- Exploit Modules: Offers a vast library of exploits to test vulnerabilities.
- Payload Delivery: Deploys various payloads for penetration testing.
- Automation: Facilitates automated testing for streamlined workflows.
Why Ethical Hackers Use Metasploit
Metasploit allows ethical hackers to simulate real-world attacks, helping organizations understand their security gaps. Its interactive features make it a go-to tool for cybersecurity professionals.
Example Use Case
A penetration tester might use Metasploit to test whether a known vulnerability in a company’s software can lead to data breaches, providing actionable insights to the development team.
3. Wireshark
Wireshark is a network protocol analyzer that provides deep insights into network traffic in real-time.
Key Features of Wireshark
- Packet Analysis: Captures and inspects individual data packets.
- Protocol Decoding: Supports hundreds of protocols, enabling detailed traffic analysis.
- Cross-Platform Support: Runs on Windows, macOS, and Linux.
Why Ethical Hackers Use Wireshark
Ethical hackers use Wireshark to identify suspicious activities in a network. By analyzing traffic patterns, they can detect potential threats like data breaches or unauthorized access attempts.
Example Use Case
When a company suspects unauthorized access to its servers, ethical hackers use Wireshark to monitor incoming and outgoing traffic, identifying malicious activity.
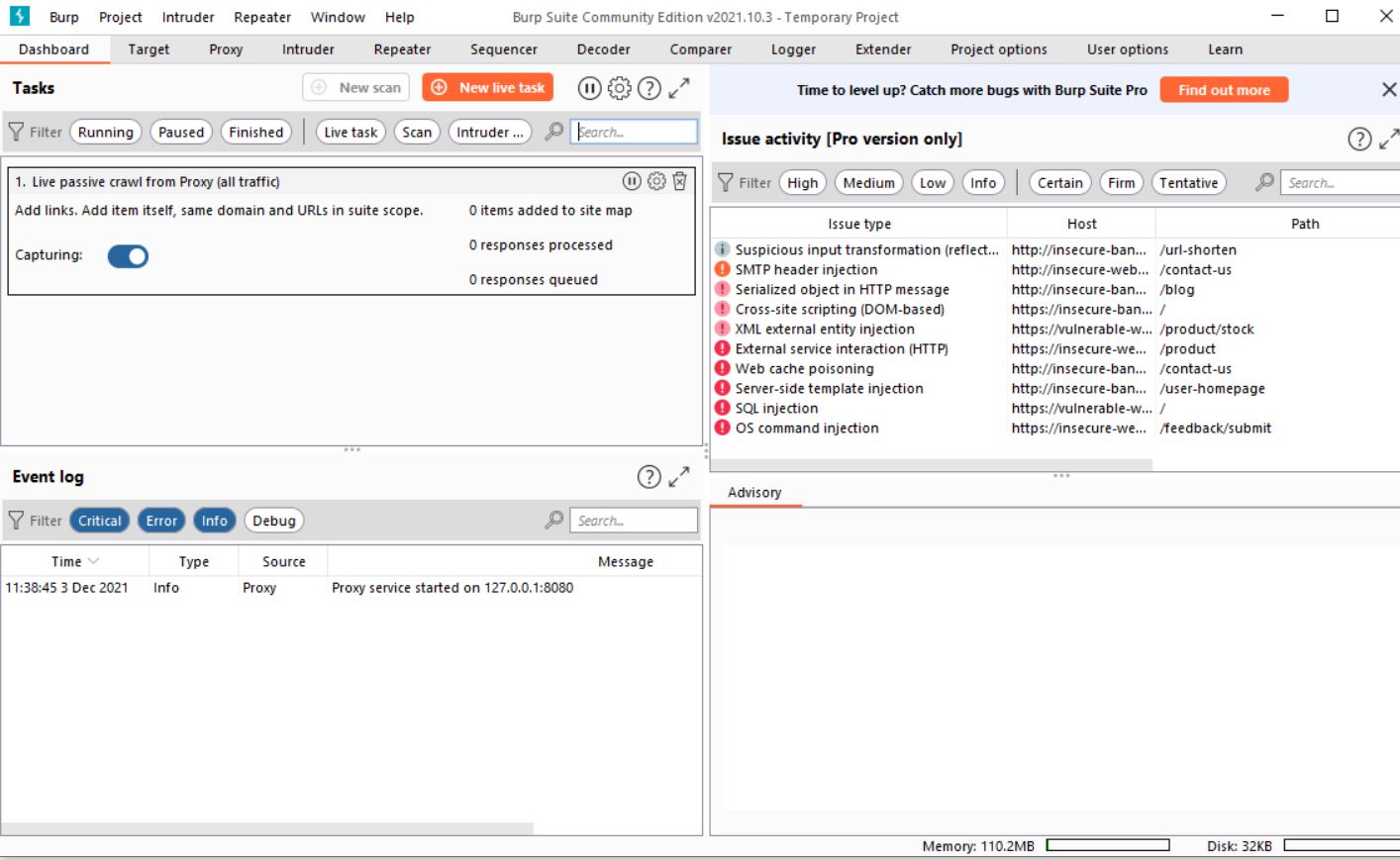
4. Burp Suite
Burp Suite is an integrated platform for web application security testing, offering tools for detecting and exploiting vulnerabilities.
Key Features of Burp Suite
- Web Vulnerability Scanning: Identifies flaws in web applications.
- Intercepting Proxy: Captures and modifies traffic between a browser and a server.
- Extensibility: Offers plugins to enhance its functionality.
Why Ethical Hackers Use Burp Suite
Burp Suite is indispensable for ethical hackers focusing on web application security. It allows for comprehensive vulnerability assessments, including testing for SQL injection, cross-site scripting (XSS), and more.
Example Use Case
Before launching a new e-commerce website, ethical hackers can use Burp Suite to test for vulnerabilities that might expose sensitive customer information.
5. John the Ripper

John the Ripper is a password-cracking tool used to test the strength of passwords and identify weak credentials.
Key Features of John the Ripper
- Customizable Wordlists: Allows users to tailor password-cracking dictionaries.
- Multi-Platform Support: Works on Linux, macOS, and Windows.
- Speed: Optimized for fast password recovery.
Why Ethical Hackers Use John the Ripper
Passwords are often the weakest link in cybersecurity. Ethical hackers use this tool to simulate brute-force attacks, helping organizations enforce stronger password policies.
Example Use Case
An ethical hacker might use John the Ripper to test whether employees’ passwords comply with an organization’s security guidelines.
6. Nikto
Nikto is an open-source web server scanner designed to identify vulnerabilities and misconfigurations.
Key Features of Nikto
- Comprehensive Scanning: Checks for outdated software and configuration errors.
- Plugin Support: Extends capabilities with additional vulnerability checks.
- Easy Integration: Works seamlessly with other penetration testing tools.
Why Ethical Hackers Use Nikto
Nikto helps ethical hackers uncover hidden security flaws in web servers. It provides actionable reports to rectify vulnerabilities before attackers exploit them.
Example Use Case
Before deploying a new web server, an ethical hacker uses Nikto to ensure the server is configured securely and free of vulnerabilities.
7. Aircrack-ng
Aircrack-ng is a suite of tools focused on assessing Wi-Fi network security.
Key Features of Aircrack-ng
- Packet Capturing: Gathers packets to analyze Wi-Fi networks.
- WEP/WPA Cracking: Tests the security of wireless encryption protocols.
- Real-Time Monitoring: Tracks network activity in real-time.
Why Ethical Hackers Use Aircrack-ng
Wireless networks are a common target for attackers. Ethical hackers use Aircrack-ng to evaluate a network’s encryption strength and identify vulnerabilities in Wi-Fi configurations.
Example Use Case
An organization looking to upgrade its Wi-Fi security can use Aircrack-ng to test the effectiveness of various encryption protocols.
8. SQLmap
SQLmap is a specialized tool for detecting and exploiting SQL injection vulnerabilities in web applications.
Key Features of SQLmap
- Automated Testing: Simplifies SQL injection testing.
- Database Support: Compatible with various database management systems.
- Advanced Features: Includes database fingerprinting, data extraction, and more.
Why Ethical Hackers Use SQLmap
SQL injection is a prevalent vulnerability in web applications. SQLmap automates the testing process, helping ethical hackers identify and mitigate these vulnerabilities efficiently.
Example Use Case
A company’s ethical hacker uses SQLmap to ensure that its database is not vulnerable to unauthorized access through SQL injection.
9. Cain and Abel
Cain and Abel is a password recovery tool that offers advanced features for ethical hackers.
Key Features of Cain and Abel
- Network Sniffing: Monitors and intercepts network traffic.
- Password Decoding: Recovers passwords stored in various formats.
- VoIP Analysis: Analyzes Voice over IP traffic for vulnerabilities.
Why Ethical Hackers Use Cain and Abel
This tool is highly effective for recovering lost credentials and testing the resilience of password storage methods.
Example Use Case
Ethical hackers use Cain and Abel to simulate attacks on password-protected files, ensuring their encryption strength.
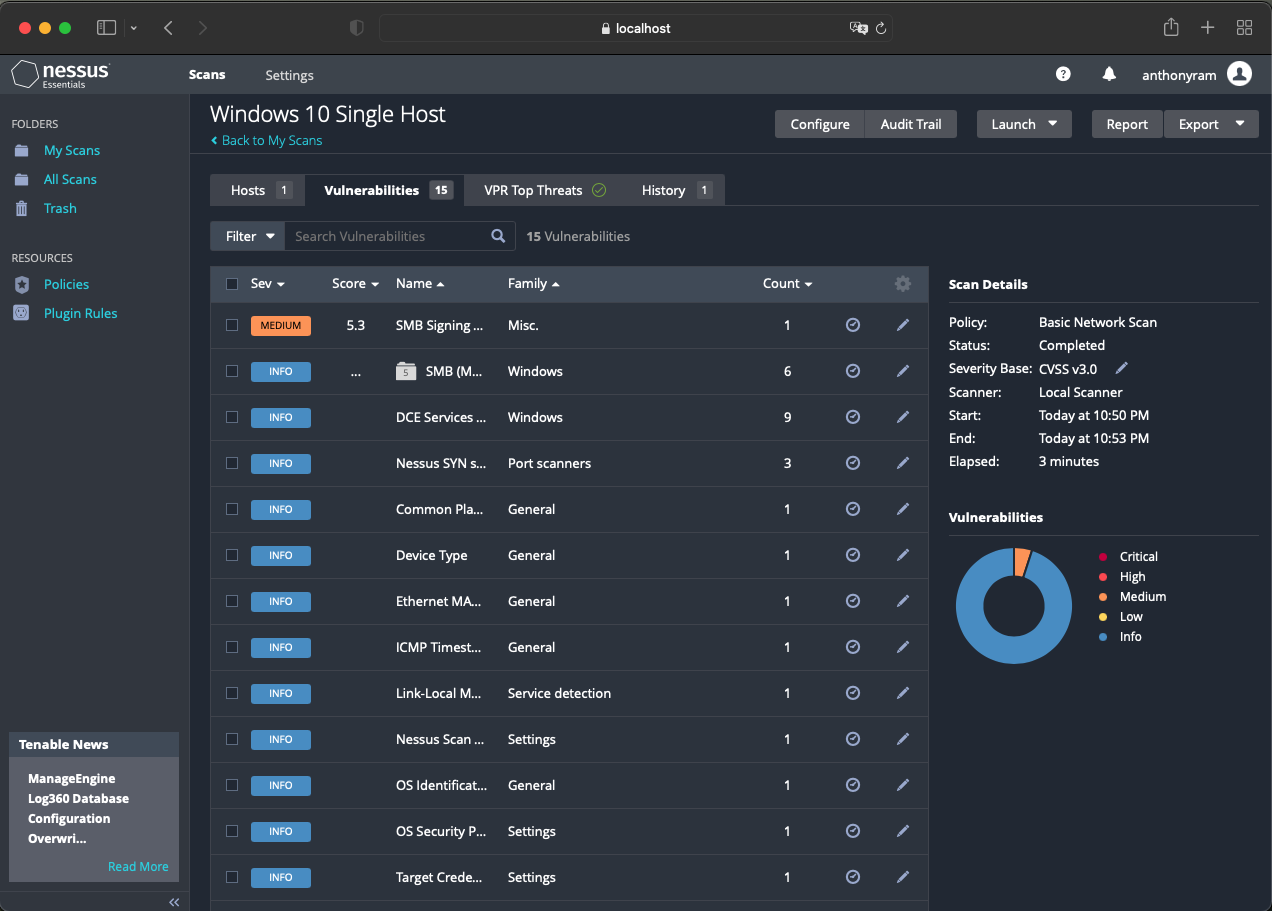
10. Nessus
Nessus is a popular vulnerability assessment tool used for identifying and prioritizing security issues.
Key Features of Nessus
- Comprehensive Scanning: Detects vulnerabilities in operating systems, networks, and applications.
- Custom Policies: Allows tailored scans for specific requirements.
- Actionable Reports: Provides detailed insights for remediation.
Why Ethical Hackers Use Nessus
Nessus helps ethical hackers prioritize security risks, enabling organizations to focus on the most critical issues first.
Example Use Case
A financial institution may use Nessus to assess its IT infrastructure for vulnerabilities, ensuring compliance with industry regulations.
Conclusion
Ethical hacking plays a pivotal role in protecting sensitive data and maintaining secure IT environments. Mastering the top 10 ethical hacking tools discussed in this article can elevate a cybersecurity professional’s skillset and effectiveness. Each tool serves a unique purpose, from network mapping to password recovery and web vulnerability testing.
By integrating these tools into their workflows, ethical hackers can stay one step ahead of potential threats, ensuring robust defenses for the organizations they serve. Whether you’re securing networks, testing applications, or evaluating system configurations, these tools are indispensable assets in the cybersecurity arsenal.